Australia is one of the most targeted countries for cyber criminals, ranking 4th in the world for phishing attacks.Companies like Australia Post, Telstra and NAB have all been targeted by sophisticated phishing attacks, but fraudsters are not only aiming at these large corporates.The number of small businesses that are being targeted has also increased, with a local business in South Australia losing $1.5m to a targeted phishing scam in October 2016 (source).When you look at the sophistication of these attacks on Google Drive and Dropbox, you can probably understand why one in four Australians cannot detect a phishing attack (source)!Esendex, together with some other SMS solution providers, have recently been targeted, so we are taking this opportunity to show you what are the latest tactics we’ve seen in play, and to give you some suggestions on how to protect yourself as a consumer and as a company to avoid falling victim to cyber criminals.
Look twice at the domain name
One of the most commonly used tactics in phishing attacks is the use of an almost identical url – with a different domain extension only.As at March 2016, there were 882 domain extensions, and while they could all be used for legitimate business, this also means hackers can use these domain extensions to create highly convincing phishing websites.Their aim, of course, is to collect personal information such as your username, password or even credit card details.This is how Esendex and other SMS companies have been targeted. Scammers purchased domain extensions like .pro, .me, .top and .pw; then made a copy of our login page so you ended up seeing something like this:
If you’re not looking closely enough, you probably couldn’t spot the differences:- The domain extension
- The use of https and the lock symbol
- The copyright notice.
And to be honest, these are probably the only differences you will find in any sophisticated phishing website.As a business, your options for preventing this from happening are unfortunately quite limited. You can use https://www.whois.net/ to find out who the registrar is and report abuse, and they should take the fraudulent website down. How long it takes, though, depends solely on the registrar.So what can you do to protect yourself and your customers? The best way is through education. Make sure your customers know the legitimate URL to access your website, and advise them of any suspected issues.
For the record, always access Esendex’s services via our brochure site at https://ops.esendex.com.au/ and use the login button at the top right, or directly at https://login.esendex.com/.
Remember, pay attention to the domain extension and always stick to recognisable ones like .com.au and .com.
Google Ads aren’t 100% reliable
Many businesses rely on Google Adwords to attract potential customers. Hackers use Google Adwords to attract potential victims too.In our case, we bid our own brand name in Google Adwords, so when someone searches for ‘Esendex’, they will see our ad as a sponsored link at the top of the result.However, any third party can also bid on Esendex’s brand name, so our hackers did too, and this is how it looked on Google UK: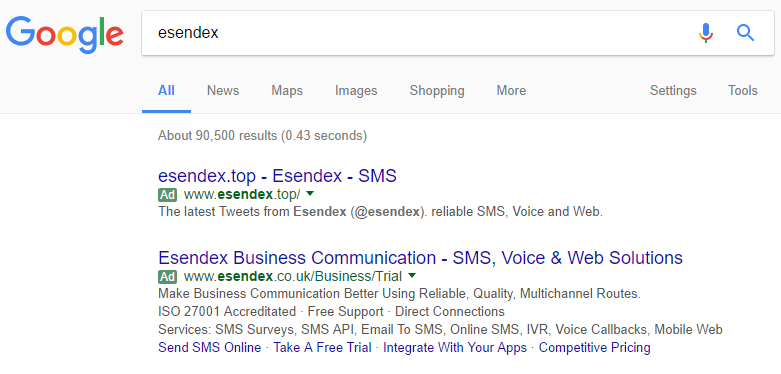
Take your password seriously
With an average person having at least 90 online accounts, ranging from emails, social media accounts, banking, utilities and government services, we really should take our password security more seriously.Yet over 50% of people use 5 or fewer passwords across their entire online life, and 47% haven’t changed their password in 5 years or more (source).If this is not convincing enough for you to go change your password now, try this: go to https://haveibeenpwned.com/ and check if your email is in one of the stolen databases among all the hacks that happened in recent years, including the breach of LinkedIn.If you found your email in there, it is a clear warning sign and you really should consider changing your password for all online services. And remember:
- Change your password every six months
- Use different passwords for each online account
- Create strong passwords (Here’s some great advice on how to).
So, what do you think readers? Have you or your business experienced phishing attacks? Share with us your experiences in the comments.


